This
could be one of the worst-ever recorded attacks of its kind - “I’ve
never seen anything like this with ransomware,"
"Worst-Ever
Recorded" Ransomware Attack Strikes Over 57,000 Users Worldwide,
Using NSA-Leaked Tools
12
May, 2017
The
ransomware has been identifed as WannaCry
*
* *
Update
4:
According to experts tracking and analyzing the worm and its
spread, this
could be one of the worst-ever recorded attacks of its kind.
The security researcher who tweets and blogs as MalwareTech told
The Intercept “I’ve
never seen anything like this with ransomware," and
"the last worm of this degree I can remember is Conficker.”
Conficker was a notorious Windows worm first spotted in 2008; it
went on to infect over nine million computers in nearly 200
countries. As
The Intercept details,
Today’s WannaCry attack appears to use an NSA exploit codenamed ETERNALBLUE, a software weapon that would have allowed the spy agency’s hackers to break into any of millions of Windows computersby exploiting a flaw in how certain version of Windows implemented a network protocol commonly used to share files and to print. Even though Microsoft fixed the ETERNALBLUE vulnerability in a March software update, the safety provided there relied on computer users keeping their systems current with the most recent updates. Clearly, as has always been the case, many people (including in governments) are not installing updates. Before, there would have been some solace in knowing that only enemies of the NSA would have to fear having ETERNALBLUE used against them–but from the moment the agency lost control of its own exploit last summer, there’s been no such assurance.
Today shows exactly what’s at stake when government hackers can’t keep their virtual weapons locked up.
As security researcher Matthew Hickey, who tracked the leaked NSA tools last month, put it, “I am actually surprised that a weaponized malware of this nature didn’t spread sooner.”
Update
3: Microsoft
has issued a statement, confirming the status the vulnerability:
Today our engineers added detection and protection against new malicious software known as Ransom:Win32.WannaCrypt.
In March, we provided a security update which provides additional protections against this potential attack.
Those who are running our free antivirus software and have Windows updates enabled, are protected.We are working with customers to provide additional assistance.
Update
2: Security
firm Kaspersky
Lab has recorded
more than 45,000 attacks in 74 countries in the past 10 hours.
Seventy-four countries around the globe have been affected, with the
number of victims still growing, according to Kaspersky Lab.
According to Avast, over 57,000 attacks have been detected worldwide,
the company said, adding that it "quickly escalated into a
massive spreading."
According
to Avast, the ransomware has also targeted Russia, Ukraine and
Taiwan. The virus is apparently the upgraded version of the
ransomware that first appeared in February. Believed to be affecting
only Windows operated computers, it changes the affected file
extension names to ".WNCRY." It then drops ransom notes to
a user in a text file, demanding $300 worth of bitcoins to be paid to
unlock the infected files within a certain period of time.
While
the victim's wallpaper is being changed, affected users also see a
countdown timer to remind them of the limited time they have to pay
the ransom. If they fail to pay, their data will be deleted,
cybercriminals warn. According to the New York Times, citing security
experts, the ransomware exploits a "vulnerability that was
discovered and developed by the National Security Agency (NSA)."
The hacking tool was leaked by a group calling itself the Shadow
Brokers, the report said, adding, that it has been distributing the
stolen NSA hacking tools online since last year.
Predictably,
Edward Snowden - who has been warning about just such an eventuality
- chimed in on Twitter,
saying "Whoa:
@NSAGov decision to build attack tools targeting US software now
threatens the lives of hospital patients."
*
* *
Update
1:
In a shocking revelation, The
FT reports that
hackers responsible for the wave of cyber attacks that struck
organisations across the globe used
tools stolen from the US National Security Agency.
A
hacking tool known as “eternal blue”, developed by US spies has
been weaponised by the hackers to super-charge an existing form of
ransomware known as WannaCry, three
senior cyber security analysts said. Their reading of events was
confirmed by western security officials who are still scrambling to
contain the spread of the attack. The NSA’s eternal blue exploit
allows the malware to spread through file-sharing protocols set up
across organisations, many of which span the globe.
As
Sam Coates summed up...
*
* *
We
earlier reported in the disturbing fact that hospitals
across the United Kingdom had gone dark due
to a massive cyber-attack...
Hospitals across the UK have been hit by what appears to be a major, nationwide cyber-attack, resulting in the loss of phonelines and computers, with many hospitals going "dark" and some diverting all but emergency patients elsewhere. At some hospitals patients are being told not to come to A&E with all non-urgent operations cancelled, the BBC reports.
The UK National Health Service said: “We’re aware that a number of trusts that have reported potential issues to the CareCERT team. We believe it to be ransomware.” It added that trusts and hospitals in London, Blackburn, Nottingham, Cumbria and Hertfordshire have been affected and are reporting IT failures, in some cases meaning there is no way of operating phones or computers.
At Lister Hospital in Stevenage, the telephone and computer system has been fully disabled in an attempt to fend off the attack.
NHS England says it is aware of the issue and is looking into it.
UK
Prime Minister Theresa
May confirms today's massive cyber hit on NHS is part of wider
international attack and
there is no evidence patient data has been compromised.
Screenshots
of a well known program that locks computers and demands a payment in
Bitcoin have been shared online by parties claiming to be affected.
It
is not
yet clear whether the attacks are all connected. One
cyber-security researcher tweeted that he haddetected
36,000 instances of the ransomware,
called WannaCry and variants of that name.
"This is huge," he said.
There
have been reports of infections in the UK,
US, China, Russia, Spain, Italy, Vietnam, Taiwan and others.
Telecoms giant Telefonica said in a statement that it was aware of a "cybersecurity incident" but that clients and services had not been affected.
Power firm Iberdrola and utility provider Gas Natural were also reported to have suffered from the outbreak.
There were reports that staff at the firms were told to turn off their computers.
In
Italy, one
user shared images appearing to show a university computer lab with
machines locked by the same program.
Bitcoin
wallets seemingly associated with the ransomware were reported to
have already started filling up with cash.
"This is a major cyber attack, impacting organisations across Europe at a scale I've never seen before,"said security architect Kevin Beaumont.
According
to security firm Check Point, the version of the ransomware that
appeared today is a new variant.
"Even so, it's spreading fast," said Aatish Pattni, head of threat prevention for northern Europe.
Several
experts monitoring the situation have linked
the attacks to vulnerabilities released by a group known as The
Shadow Brokers, which
recently claimed to have dumped hacking tools stolen from the NSA.
A
massive cyber attack demanding ransoms appears to have infected a
number of organisations around the world.
There
have been reports of infections in as many as 74 countries, including
several in New Zealand, a
live-tracking map of the attack shows.

Hospital
computers across Britain shut down by cyberattack, hackers demanding
ransom

RT,
12
May, 2017
Hospitals
across Britain have been hit by a large-scale cyberattack. Some are
having to divert emergency patients, with doctors reporting messages
demanding money.
National
Health Service (NHS) hospitals across the country were hit by a bug
spreading through their IT systems. Doctors have been posting on
Twitter about what has been happening.
Here's what a London GP sees when trying to connect to the NHS network
NHS
Digital which has responsibility for IT systems says the attack is
not believed to have been a targeted one. It has named the malware
'Wanna Decryptor' as the likely cause of the problem, but insists
there is no evidence that patient data has been accessed.
Prime
Minister Theresa May is being kept informed on the situation, a
spokesperson for her office told Reuters, while health minister
Jeremy Hunt has been briefed by cyber security officials.
Our statement on the reported ransomware issues: https://digital.nhs.uk/article/1491/Statement-on-reported-NHS-cyber-attack …
#nhscyberattack
A
screengrab of an instant message conversation circulated by one
doctor says: “So our hospital is down … We got a message saying
your computers are now under their control and pay a certain amount
of money. And now everything is gone.”
A
second doctor tweeted: “Massive NHS hack cyber attack today.
Hospital in shut down. Thanks for delaying emergency patient care &
endangering lives. Assholes.”
East
and North Hertfordshire NHS Trust, one of those affected, said in a
statement: “Today, the trust has experienced a major IT problem,
believed to be caused by a cyber attack.
Why would you cyber attack a hospital and hold it for ransom? The state of the world 

“Immediately
on discovery of the problem, the trust acted to protect its IT
systems by shutting them down; it also meant that the trust’s
telephone system is not able to accept incoming calls.
“The
trust is postponing all non-urgent activity for today and is asking
people not to come to A&E.”
Someone as hacked into the computer network at Royal Blackburn Hospital!! Can't give out prescriptions to anyone!!!!
Blackpool
Hospitals, also affected, tweeted: “Our computer systems are
experiencing problems and we are working hard on a solution. We will
update you as soon as possible.”
Sky
News reported that sources inside the department of health had
described the attack as "unexpected, but not unprecedented."
NW hospital computer systems under cyber attack 4 ransom... Sitting in front of a blank screen & can't do any work. Criminal Poor patients

According
to reports, affected hospitals include those run by East and North
Hertfordshire NHS trust, Barts Health in London, Essex Partnership
university NHS trusts, the university hospitals of Morecambe Bay NHS
foundation trust, Southport and Ormskirk hospital NHS trust and
Blackpool teaching hospital NHS foundation trust.
Services
affected are thought to include picture archiving communication
systems for x-ray images, pathology test results, phone and bleep
systems and patient administration systems, the Telegraph reports.
We apologise but we are having issues with our computer systems. Please don't attend A&E unless it's an emergency. Thanks for your patience
“At
approximately 12:30pm we experienced a problem with our email servers
crashing. Following this a lot of our clinical systems and patient
systems were reported to have gone down,” an NHS IT worker said in
a message to a Guardian reporter.
“A
bitcoin pop-up message had been introduced onto the network asking
users to pay $300 to be able to access their PCs. You cannot get past
this screen.
“This
followed with an internal major incident being declared and advised
all staff to shut down all PCs in the trust and await further
instructions.”
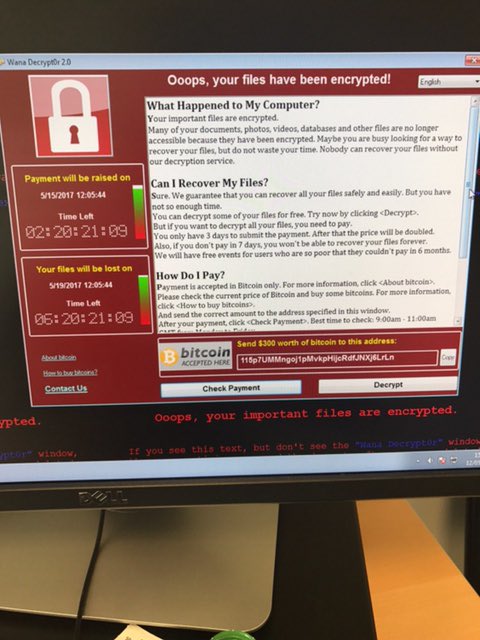
There
are reports of messages on computers saying: “Oops. Your files have
been encrypted,” and demands for bitcoin to be paid.
The
hack appears to be an example of ransomware, where malicious hackers
break into computers and only allow their owners back in when they
pay enough money.
The
attackers are allegedly demanding $300-worth (£232) of the digital
currency bitcoin, otherwise the files will be deleted. It gives a
deadline of May 19 to pay.
A
screenshot obtained by the Health Service Journal (HSJ) purported to
show the pop-up that appeared on at least one of the computers
affected.
It
said: “Your important files are encrypted. Maybe you are busy
looking for a way to recover your files, but do not waste your time.
“Nobody
can recover your files without our decryption service.”
On
Friday, Spain’s government warned that large numbers of companies
had been attacked by cyber criminals who infected computers with the
same ransomware used on the NHS.
The
victims included Telefonica, the nation’s biggest
telecommunications firm.
Here
is coverage from the Guardian. Will they find a way of blaming Russia
even thought the majority of attacks are on Russia, including the
Ministry of Internal Affairs
- Report: Massive ransomware cyber-attack hits over 74 countries
- This is not targeted at the NHS, it’s an international attack, says Theresa May
- NHS England declares major incident after ransomware blocks access to patient records, internal phones and mails
"Massive Disturbances" In German Rail System Due To Ransomware Attack
Germany's
WAZ reports massive
disturbances in local and long-distance rail traffic on Friday
evening due
to what appears to be the same ransomware attack that is spreading
across the globe.
Numerous social media
accounts are showing the following images...
More details to follow...
Local reports say that
the situation in Germany is getting
chaotic.

















































No comments:
Post a Comment
Note: only a member of this blog may post a comment.