WannaCry
ransomware shares code with North Korea-linked malware –
researchers

RT,
16
May, 2017
The
source for WannaCry ransomware, which has spread to 150 countries,
may be Pyongyang or those trying to frame it, security analysts say,
pointing to code similarities between the virus and a malware
attributed to alleged hackers from North Korea.
The
speculation over a North Korean connection arose Monday, after the
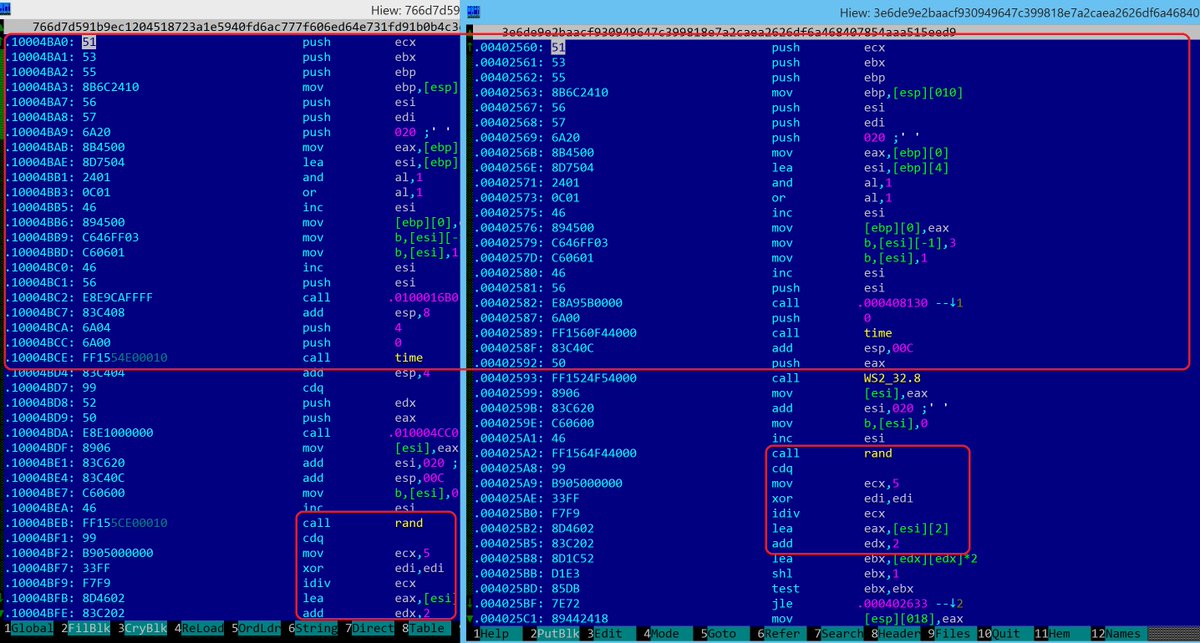
well-known Google security researcher Neel Mehta revealed a
resemblance between the code used in what is said to be an early
version of WannaCry ransomware and that in a hacker tool attributed
to the notorious Lazarus Group in a Twitter post.
9c7c7149387a1c79679a87dd1ba755bc @ 0x402560, 0x40F598
ac21c8ad899727137c4b94458d7aa8d8 @ 0x10004ba0, 0x10012AA4
#WannaCryptAttribution
Containing
what might look like a random set of figures and letters to an
outsider accompanied by the hashtag #WannaCryptAttribution, the post
has immediately drawn attention of cybersecurity experts and has been
since extensively shared.
Shedding light on the otherwise cryptic message, Kaspersky Lab explained in a blog post that Mehta drew parallels between “a WannaCry cryptor sample from February 2017” and “a Lazarus APT [Advanced Persistent Threat] group sample from February 2015.”
Shared code between an early, Feb 2017 Wannacry cryptor and a Lazarus group backdoor from 2015 found by @neelmehta from Google.
Shedding light on the otherwise cryptic message, Kaspersky Lab explained in a blog post that Mehta drew parallels between “a WannaCry cryptor sample from February 2017” and “a Lazarus APT [Advanced Persistent Threat] group sample from February 2015.”
Labelling
Mehta’s revelation “the
most significant clue to date regarding the origins of
WannaCry,” Kaspersky
researches at the same time acknowledged that the apparent use by the
WannaCry attackers of the similar code is not enough to come to
definitive conclusions about its origin, as there is a possibility of
it being a false flag operation and more international effort is
necessary to unearth its roots.
“It’s important that other researchers around the world investigate these similarities,” the post reads.
At
the same time, they said there is little doubt that February 2017
code, referenced by Mehta, “was
compiled by the same people, or by people with access to the same
source code” as
the current spree of attacks.
Another
renowned researcher, Matthieu Suiche from Comae Technologies, also
said on Twitter that the discovered code similarities might have put
security experts on the trail of the hackers.
Similitude between #WannaCry and Contopee from Lazarus Group ! thx @neelmehta - Is DPRK behind #WannaCry ?
“WannaCry
and this [program] attributed to Lazarus are sharing code that’s
unique. This group might be behind WannaCry also,” Suiche
said, as cited by Wired.
However,
he agreed with Kaspersky researchers that it would be wrong to rush
to pin the blame on North Korea, based on these assumptions.
“Attribution
can always be faked, as it’s only a matter of moving bytes
around,” Suiche
said, as cited byCyberscoop.
Meanwhile,
American security giant Symantec voiced a similar opinion in a
statement Monday. Saying that it had discovered a code used in the
malware that “historically
was unique to Lazarus tools,” the
company refused to
speculate on North Korea’s role in the attack.
“We
have not yet been able to confirm the Lazarus tools deployed WannaCry
on these systems,” it
stressed.
The
Lazarus Group is believed to be behind numerous high-profile hacking
attacks on banks’ SWIFT servers, including an attempt to steal $851
million from Bangladesh Central Bank last February and is deemed to
be responsible for the November 2014 Sony Pictures hack.
While
no compelling proof that would implicate North Korea or other state
actor in the array of cyber heists has been revealed, some of the
evidence uncovered by Russian multinational cybersecurity and
anti-virus provider, Kaspersky Lab, last month, appears to support
the speculation.
In
an April 3 blog
post,
Kaspersky Lab's Global Research & Analysis Team said that it had
traced some of the IPs used by the Lazarus attackers back to North
Korea, thus for the first time establishing “a
direct link” between
the suspected cyber criminals involved in the Lazarus operations and
the rogue state. However, Kaspersky experts then fell short of naming
North Korea a culprit, citing lack of evidence.
“Now,
is it North Korea behind all the Bluenoroff attacks after all? As
researchers, we prefer to provide facts rather than
speculations,” they
wrote.
The
ransomware began its global spread on Friday. Dubbed WannaCry, it
exploits vulnerability in the Windows operating system that was first
discovered by the National Security Agency (NSA) and was later leaked
to public by the hacker group the Shadow Brokers last month,
prompting Windows to close the loophole and issued an update. Once
the malware infects the system, it sends the user a text file with a
ransom demand for some $300 worth of Bitcoins. It also installs a
countdown timer on the victim’s wallpaper, demanding to pay the
ransom if one does not want private files delete.
Among
the notable victims affected by the virus were the National Health
Service (NHS) hospitals in the UK, Russia’s Interior Ministry,
Spain’s telecommunications company Telefonica and reportedly some
Chinese government agencies.
Speaking
in Beijing on Sunday, Russian President Vladimir Putin called on the
international community to offer a coordinated response to the
cybersecurity threats at “the
highest political level” and
lamented the US’s refusal to discuss the issue with Russia. The
Russian leader also cited another theory on the origin of the
malware, stating that “Microsoft’s
management has made it clear that the virus originated from US
intelligence services.”
Meanwhile,
cyber security firm Check Point Software Technologies Ltd said that
it had discovered and neutralized the updated version of the WannaCry
on Monday by successfully initiating what it called a “kill
switch” inside
the software.
The
spread of WannaCry ransomware seems to be well past its peak, the
22-year-old security expert Marcus Hutchins who is in the forefront
of the battle against the virus told AP. The attack is “done
and dusted” thanks
to the accumulated effort of hundreds of specialists over the
weekend, he said.































No comments:
Post a Comment
Note: only a member of this blog may post a comment.