DIGITAL
ARMAGEDDON - Source Code for Top 3 US Anti-Virus Makers Reportedly
Stolen. ALL Critical Infrastructure Now Vulnerable
4 June, 2019
The source codes of three American antivirus manufacturers were reportedly stolen and have allegedly been cracked. Anyone with the money can obtain the codes - including organized crime. Another aspect is more dramatic: almost all critical infrastructures in the West are now vulnerable." This is literally Digital Armageddon.
Fxmsp hacker group is claiming access to the networks and source code of three antivirus companies with offices in the U.S.
Up until this week, the names of the victims (Symantec, McAfee and Trend Micro) remained undisclosed to the public due to the sensitive nature of the matter and because authorities had been alerted of the incidents.
But the cat's out of the bag right now, as the victim antivirus companies have released statements that either downplay, contradict the findings, or have decided to neither deny nor confirm the incident.
Un-redacted evidence from fraud prevention company AdvIntel showing communication from the Fxmsp hacker collective naming three of the victims.
AdvIntel has collected information about the activity of Fxmsp and its sellers on underground forums (mostly Russian speaking) and gathered instant messaging logs of the actor discussing their access and trove of data they were advertising to sell for up to $300,000.
Below is a conversation about source code files for various products from antivirus companies Symantec, McAfee, and Trend Micro. The chat is between Fxmsp members:

Here's an adapted version of the translated image:
(1:26:03) uwerty5411(@exploit.im: I already have outcomes
(1:26:23)
plz? same price?
: can throw a screen,
(1:27:17) uwerty5411@exploit.im: there are 350 developments of the company, antivirus, kernels, artificial intelligence, web protection, panels, everything that a company has, even those developments that only large corporations
(1:27:26)
: Okay, you can without
screenshots, this is too much
((1:27:29) uwerty5411@exploit.im: the same price
((1:28:07) uwerty5411@exploit.im: screenshots are meaningless, but I can show through AnyDesq
(17:29:27) fxmsp: if 100-200 then McAfee
(17:29:36) fxmsp: if 50-100 the Norton
(17:29:44) fxmsp: if 300-350 the trend
developments?
(17:30:09) fxmsp: number of files
(17:30:37) fxmsp: sorts of concept extensible
((17:31:22) fxmsp: each antivirus has its own development on past antiviruses, there is are web building versions, there are all sorts of utilities, such as a TeamViewer
(17:31:49) fxmsp: there are antiviri under POS terminals
(17:31:58) fxmsp: mail them a crapload of antivirals each
AdvIntel said they have the following evidence supporting their findings and the release of the report last week:
(1) Full chat logs listing all the 3 identified anti-virus names (and more) breached as disclosed by the actor;
(2) Full video recording from the actor assets regarding their operation;
(3) Full source code samples from at least one of the AV vendors breached as obtained from the actor;
(2) Full video recording from the actor assets regarding their operation;
(3) Full source code samples from at least one of the AV vendors breached as obtained from the actor;
The company also has a screenshot showing the properties of a video file to support their findings. According to AdvIntel, the video shows content from the hop server and transfer of gigabytes of data from the compromised antivirus company, with file timestamps, actor commentary, source code, and walkthrough of the actual code.
Exclusive Fxmsp chat logs
Snapshots of conversations between Fxmsp group members about their presence into the network of the three antivirus companies are shown below. Yelisey Boguslavskiy, director of security research at AdvIntel, provided them along with a translation into English. Only the names Trend Micro and McAfee appear in these chats.
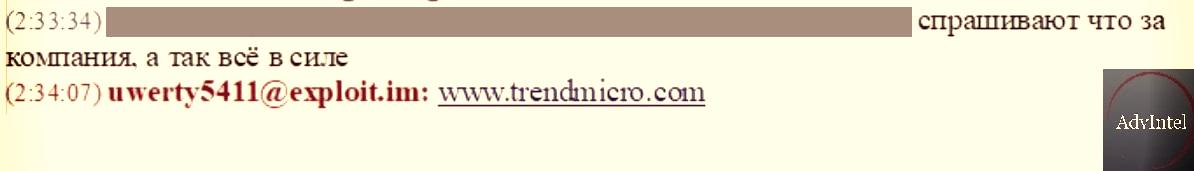
Here's the translation of the chat log:
What is the company?
Fxmsp: trendmicro[.]com
Fxmsp talked about getting into the network of Trend Micro and stealing source code from the company, all without triggering detection. This was possible after exploiting a vulnerability, according to their conversation below.
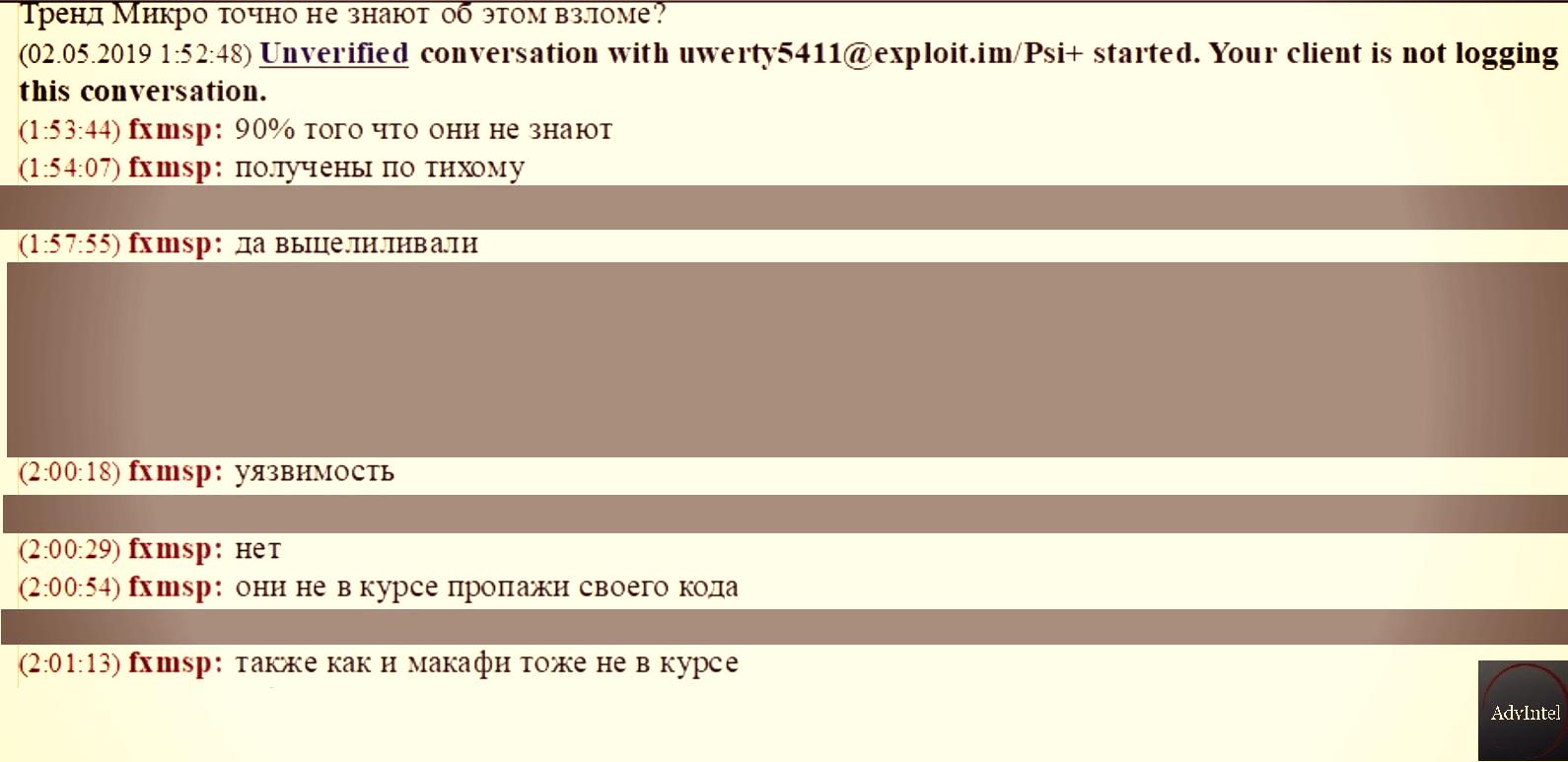
Here's the translation of the chat log:
Is Trend Micro aware of the breach?
How did you get access? TrendMicro do not know about it?
Fxmsp: 90% they have no idea
Fmxsp: we got it covertly
Fmxsp: yes [we] targeted them specifically
Fxmsp: [there was a] vulnerability
Fmxsp: they have no idea they lost their source code
Fxmsp: also McAfee has no idea we got them
The hackers talk about the volume of data they found on a victim's network.

Here's the translation of the chat log:
Developments?
Fxmsp: quantity of all files [is huge]
Fxmsp: source code is a wide term
Fmxsp: every antivirus has its own soft development outside of web, corporate, and other utilities, TeamViewer-like
Fmxsp: They have point-of-sale anti-virus as well
Fmxsp: Email AV, they have every type possible
Fxmsp group members discuss about how they can move inside the network of a victim antivirus company and how they could connect without setting off an alarm.

Here's the translation of the chat log:
Fxmsp: the [TrendMicro] access is to a local corporate network
Fxmsp: you have unfettered access in their network environment
Fxmsp: no, you can only move laterally via credentialed net shares or RDP
Fxmsp: the access sold is via TeamViewer or AnyDesk remote software
Fxmsp: their network defense does not see us b/c teamViewer and AnyDesk are legit software, and admins also use it there. That is why no questions.
Fxmsp: their [TrendMicro] network is huge and every network portion has different visibility
Fxmsp: when downloading and exfiltrating all the [TrendMicro] data it will over 1000 terabytes
Fxmsp: plus when exfiltrating all their data, it would take months, very risky to exfiltrate everything that they have
Fxmsp was convinced that no one was watching them roaming inside the network of antivirus companies and that their intrusion would be discovered only if the data they stole and sold got leaked online.

Here's the translation of the chat log:
Fxmsp: Everything is quiet. All of them [AV companies & law enforcement] will know that something is missing from them is only if the information becomes available on the web.The official statements
AdvIntel told us that last week they had contacted all three antivirus vendors. They reached out to Symantec via trusted partners on May 8 "and had two remediation calls on May 9 and May 10, respectively."
Multiple news outlets received a statement from Symantec denying having been contacted by AdvIntel researchers. Others also received such a statement, from someone working at Symantec's agency of record, Eldman, asking for a correction in articles detailing Fxmsp activities and presenting new evidence.
A few hours later media outlets received an updated statement saying:
"Symantec is aware of recent claims that a number of US-based antivirus companies have been breached. We have been in contact with researchers at AdvIntel, who confirmed that Symantec (Norton) has not been impacted. We do not believe there is reason for our customers to be concerned."
A statement we received from AdvIntel agrees with Symantec's comment, noting that more proof was required in order to conclude that an unauthorized entity was indeed present on Symantec's network.
AdvIntel works directly with Symantec to mitigate the risk. Even though Fxmsp collective claimed that the company is in the victim list, they have not provided any sufficient evidence to support this allegation. We believe with a high degree of confidence that Symantec's assessment of risks and their statement that "there is no reason for our [Symantec] customers to be concerned currently" is correct.
AdvIntel says that Trend Micro was the first of the companies they contacted, on April 24, because they had obtained information about them first.
We also reached out to Trend Micro for a statement about the reported Fxmsp breach of their networks. A company representative sent us the following official reply:
"We have an active investigation underway related to recent claims, and while it is not complete, we want to transparently share what we have learned. Working closely with law enforcement, our global threat research and forensic teams are leading this investigation. At this moment, we are aware that unauthorized access had been made to a single testing lab network by a third party and some low-risk debugging related information was obtained. We are nearing the end of our investigation and at this time we have seen no indication that any customer data nor source code were accessed or exfiltrated. Immediate action was taken to quarantine the lab and additionally secure all corresponding environments. Due to the active nature of the investigation, we are not in a position to share any additional information, but we will provide an update when additional insights become available and can be disclosed."
- Trend Micro spokeperson -
According to Boguslavskiy, Trend Micro's statement is incorrect.
"As for Trend Micro report regarding source codes, we can provide evidence of the actual files taken (more than 100 MB of the sym files) that the actor had access with over 30TB of source code and everything from TrendMicro," the researcher told BleepingComputer.
McAfee was also contacted on May 9, Boguslavskiy says, as did we today; however, at the time of writing we are still waiting for a reply from the company.
Responding to our request for comment, McAfee neither denied nor confirmed the breach, saying that they are monitoring the matter and conducting an investigation:
"McAfee is aware of this threat claim targeting the industry. We’ve taken necessary steps to monitor for and investigate it."
In an email, Boguslavskiy says that AdvIntel directly notified the FBI on May 4 about the recent activities of the Fxmsp threat actor.




No comments:
Post a Comment
Note: only a member of this blog may post a comment.